SEQRITE: PRACTICAL APPLICATION OF MDM FOR COMPLETE CONTROL OVER MOBILE DEVICES
- trendsbird
- August 18, 2021
- Uncategorized
- No Comments
The progressive version of the Android operating system encapsulation does not make it easy for developers of security solutions. With each subsequent installment, access to critical areas of the Android system is limited. The basic problem (ironically!) Is the sandbox – if the installed application tries to perform an undesirable activity, eg to gain access to private data from another application, then the separated area in which the “program A” is running will not allow access to information from ” program B “, unless this operation is preceded by the deliberate use of the 0-day vulnerability and escape from the isolated memory area.
In practice, Android does not allow mobile antivirus to get higher privileges than installed programs from the official repository. As a consequence, without access to root, you can not remove system applications, seriously infect your system, install some open-source “apps” from the alternative F-Droid store or block ads using the great AdAway application (except for the mobile Firefox with the uBlock extension and Opera browser with ad blocking function). In fact, anti-virus protection secures the user’s area with the same level of privileges as any other installed application. Thus, it comes to a strange situation in which malware getting root will have higher privileges than antivirus. This problem was partially solved by introducing the role of device administrators (although this is not the same as “root”). The installed application then obtains access to privileged permissions, which allows:
- Control the change in the way the device is locked.
- Block the multimedia functions of the smartphone, eg the camera, the voice recorder.
- Block NFC, Wi-Fi, Bluetooth, calls and SMS messages.
- Block the function of restoring factory settings.
- Remotely erase data.
- Install or delete applications.
- Enforce using, for example, GPS.
Malicious applications often try to get root privileges to make it difficult to detect and delete. Of course, mobile anti-viruses are not in a losing position because they constantly scan websites, files on the SD card, SMS messages, downloaded files and applications from the official and unofficial repository. However, it is very difficult to uninstall a malicious application that somehow has obtained root privileges or a device administrator role. If this happens, usually you should enable the debug mode in the advanced settings of development tools, pair the device from the PC and use the console to remove the threat or simply to system, or install a virus-free clean image of the Android system. Rooting a smartphone is not entirely obvious – it can cause a lot of problems for non-technical users, including the loss of the manufacturer’s warranty.
In the summer of 2017, Google launched a global Google Play Protect service for all Android devices. It is an antivirus integrated with the Google Play store.
The mandatory application is also “Find my device”.
The main difference between the “Find my device” functionality introduced by Google and similar programs to locate the location of a smartphone is the ability to delete data from an Android phone or tablet, or a Wear watch. However, this stick has two ends – privacy is a factor that can collect negative comments.
Localized device using the “Find my device” function built into the Android system.
Putting Google’s ideas into practice is a step in the right direction, but the security problems are still not to be solved at this level of Android technological thought. A company from Mountain View has proven more than once that it can not cope with the malware distribution chain by updating malicious applications located in the store . It also does not cope with preinstalled malware on new devices . In addition, the developers of Android and iOS are increasingly closing their environment to third parties, and this does not make work easier for software suppliers and security services. Is it wrong? No, but without a clear plan for the future it is difficult to plan your business for several years ahead. Manufacturers, in order not to be far behind, have to look for other sales areas of their value-added services. The sooner they do, the better.
THREE FACTORS OF PREVENTIVE PROTECTION OF IT AREAS WITH SEQRITE
1. ACCESS CONTROL
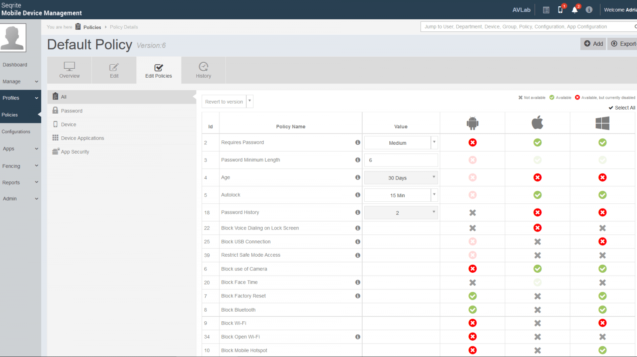
If a “foreign” device is logged into the company network, we can assume that the network is not sufficiently secured. An unknown device should not have access to all company areas. It does not matter if it is a laptop, private or business smartphone. Securing data against recognition, burglary and theft must be a priority for many entrepreneurs. Additional protection of access to the corporate network can be obtained after the implementation of the popular RADIUS protocol (supported by most popular routers), which will authorize the device and authenticate the user on the network. If we add the MDM solution (Mobile Device Management), which will enforce the access policies of mobile devices in wireless networks and access to resources on servers and cloud services, we will get a solid foundation for secure configuration of the company policy. The Mobile Device Management product will separate the private and business zone by managing the zone with company applications for users of mobile systems and, if necessary, block the basic functions of the phone. The earlier and better we secure the IT area, the less time and resources we devote to analyzing the digital intrusion.
The Seqrite company adhered to international guidelines already at the stage of designing the Seqrite Mobile Device Management software. The ISO 9001, ISO 20000 and ISO 27001 certifications confirm the modern standards of IT service management (for which the company needs to pay tribute) – and what is connected with it – guarantee a high level of quality of the services provided.
2. APPLICATION MONITORING
In order to increase protection against a potentially malicious application (yes, Google Play contains a lot of malicious programs, in addition can not cope with their detection) Seqrite Mobile Device Management can block attempts to install applications from Google Play, iTunes, App Store, Windows Phone Store or from APK files. Administrators can refuse to install programs from predefined categories (eg games, instant messengers, social media), but this change can be made the other way – the Seqrite MDM agent will force installation of recommended company applications that will be downloaded and installed from official repositories (or from an APK file) with one click of an employee.
Seqrite Mobile Device Management allows you to create a safe work environment without any problems. We have a situation in which using only recommended applications will effectively discourage users from circumventing restrictions. After all, the business phone is the property of the company, not the employee, and the company sets the rules. Allowing privacy on a work phone is a privilege, not an obligation. Even after business hours. Selected applications in a cloud console can be managed, installed or blocked in a very simple way. The compatibility of the installed programs and system settings with the company’s policy guarantee a safe and almost unbreakable environment.
3. PROTECTION
The Seqrite Mobile Device Management solution is a product that supports security in a wide range. It enables significant control over protected company resources and installed applications, but above all it secures the area of mobile systems against malware supply chains.
A lightweight agent installed on the end device, which has an anti-virus engine, which has been repeatedly awarded in independent tests , verifies the security of applications that might attempt to gain elevated privileges and seriously infect the operating system. Several protective layers, including a website scanner that distributes malware and phishing, will block attempts to display fake installers. Should this be necessary, the administrator can add a web address or IP address to the exceptions and thereby permanently block or unblock the online resource on all mobile devices.
MULTI-STAGE ATTACKS
By controlling the installed applications, eg using the proprietary Seqrite launcher or managing installed applications remotely (and adding those undesirable to the blacklist), we limit the risk of using the exploit, not only software, but also hardware. When at the end of 2016, researchers from VUSec Labs, the University of California and the University of Technology in Graz discovered a security gap in smartphones working under the control of the Android operating system, the world learned that there is a way to get root privileges without interacting with the user.
Drammer was the first Android exploit that gave the highest permissions without exploiting any vulnerability in the system or in installed applications. By manipulating the data in memory and changing some of the bit sequences from 0 to 1 and vice versa, you could get root on some devices. As a result, remotely installing malware is a matter of a few commands. Most importantly, there is no way to defend against such attacks on vulnerable DRAMs – in theory the researchers gained access to the device by connecting it with a PC, but in practice you can arm the drive-by download attack into an exploit and install malware (although this will require interaction with user).
For companies and individual users, drive-by download attacks are a real nightmare. It is difficult to detect them, and in addition, the infection of the operating system usually takes place without interaction with the person sitting in front of the monitor. In the case of Android, the authors of the malware used the bug in the Google Chrome mobile browser. Normally, when downloading a file, the user must allow the downloading of data. However, the APK file can be split into 1024-byte pieces that are passed to the write function via the Blob () class, so without the user’s knowledge the application will write on the device piece-by-piece. After downloading, the file will be reconstructed into a malicious application. The weakest link in this trick is interaction with the user – without installing the program, the Trojan will simply remain on the smartphone in the form of a harmless file. However, this does not change the fact that the technique of downloading the resource from a remote server to a mobile device – and without interaction with the user – has been used in real attacks.
Seqrite MDM for problems with mobile devices
Android security issues are still unresolved by Google. Theorizing, since the user has to download and install the malicious application himself (or with the help of social engineering), in practice no serious infection should ever happen. The latest information about the KRACK vulnerability kit for WPA2 and vulnerable to remote attacks of Bluetooth wireless communication prove that each smartphone can be a potential carrier of an infection that actively searches for another vulnerable device.
In working environments particularly sensitive due to processed information (eg banks or hospitals), the solution of the Mobile Device Management class gives its manager an advantage over cyberthreatures resulting from internal as well as external factors. Easy access to the console based on cloud technology allows the administrator to flexibly configure policies that provide a solid foundation for the security of the organization. If the devices we authorize correctly implement the use of the company’s infrastructure, we get the total visibility of all mobile smartphones connected to the company’s network. As a result, we will get full control – including a comprehensive inspection of all applications that, if managed by the administrator, will maintain policy compliance and increase employee productivity. In addition, functions such as network filtering, anti-theft protection and location tracking will ensure the security of the devices. There is nothing worse for an administrator than a ghost device that does not know who it belongs to, where it came from and what resources it has access to. In case of any problems, customers can count on technical support provided by the Polish branch of engineers and directly by the manufacturer (by phone, email or chat) 24 hours a day and 7 days a week.
In addition to the control and management functions, the Seqrite Mobile Device Management solution, as befits a product with ISO 9001, ISO 20000 and ISO 27001 certificates, can generate comprehensive and useful reports on all protected devices. It is possible, for example, to generate a report for devices that do not meet the current policy settings, because, for example, they do not have installed recommended applications or system settings are incompatible with those introduced by the administrator. It is also possible to specify information about calls and SMS messages, installed applications, or make an inventory broken down into devices, users and IMEI numbers of each smartphone and tablet.

WHAT IS THE FUTURE OF MOBILE ANTI-VIRUSES WAITING FOR?
Users’ awareness of security slowly, but systematically sticks the last nails to the lid of the mobile anti-virus software coffin. But there is nothing wrong with it that would not work out. Other areas are waiting for development, such as: active monitoring of applications, controlling the functions of a smartphone, enforcing access to company resources, or separating a private and business zone. And it is precisely on the grounds of prevention (filtered & deny) that Seqrite finds its niche by offering the security of mobile devices.
Is it worth to implement the MDM solution, just preventively, to save yourself gray hair, the costs of reproducing lost data and not to mention the consequences resulting from the GDPR? As always, the decision is conditioned by an individual approach to security.